Essential Security Protocols for Live Chat Professionals
Working remotely in a live chat job has its perks, but security risks lurk around every corner. Did you know that cyber attacks on remote workers have increased significantly since more people started working from home? This blog will guide you through easy to implement yet robust security measures for your home office, keeping your chats and data safe.
Stay secure and stay ahead; let’s dive into safeguarding your digital workspace!
Key Takeaways
- Install reliable locks, use a shredder for sensitive documents, and set up security cameras to secure your home office physically.
- Encrypt all devices using tools like BitLocker or FileVault and keep software updated to protect against cyber threats.
- Use strong passwords combined with two – factor authentication for an extra layer of digital security.
- Train employees on recognizing phishing attempts and maintaining robust cybersecurity practices while working remotely.
- Separate personal from work devices and implement regular backups to ensure data protection in case of system failures or attacks.
Security Measures for Working from Home Employees
Secure your home office by installing security cameras and alarm systems, encrypt your devices to protect sensitive information, and always keep all software and operating systems up-to-date to prevent cyber attacks.
Use strong passwords and two-factor authentication to add an extra layer of security to your online accounts.
Secure your home office
Securing your home office is a vital step in protecting precious data and maintaining privacy while working on live chat jobs. It establishes a safeguard between your work and potential security threats.
- Start by installing reliable locks on the doors and windows of your home office. This basic measure prevents unauthorized physical access.
- Equip your workspace with a shredder to destroy sensitive documents properly, ensuring they can’t be reconstructed by prying eyes.
- Set up a fireproof safe for storing important hardware like hard drives or flash drives that contain critical information.
- Install security cameras overlooking your home office entrance to monitor any unexpected visitors or activity when you’re away.
- Ensure that your Wi – Fi network is private, using WPA3 encryption, which offers the strongest available protection against hackers.
- Change the factory – set passwords on your router and other devices to unique passcodes that mix letters, numbers, and symbols.
- Place privacy screens on your monitors to prevent anyone from peeking at confidential information from different angles in shared spaces.
- Keep personal devices separate from work devices; this limits the risk of cross – contamination if one device gets compromised.
- Regularly backup all your work to an off – site location or cloud service; this prepares you for data recovery in case of system failures or attacks.
- Securely manage the physical keys or access cards to your home office, ensuring they are not easily accessible to others outside of work hours.
Encrypt your devices
Once you’ve fortified your physical workspace, take a critical step to shield your digital life: device encryption. This powerful security measure converts your data into code that unauthorized users can’t easily decipher.
On laptops, desktops, and mobile devices alike, encryption acts like an unbreakable lock on the sensitive information stored within them.
Enable full-disk encryption tools native to your operating system, such as BitLocker for Windows or FileVault for macOS. Don’t overlook encrypting external storage devices too—USB drives and external hard drives can be secured with software designed for this purpose.
Make sure all of your gadgets are encrypted to create a robust barrier against cyber intruders aiming to access confidential work information from your home office setup in a live chat job or any other remote position.
Keep all software and operating systems up-to-date
Updating your software and operating systems is vital for home office security. It shields you from vulnerabilities and cyber threats.
- Check for updates on all your devices regularly, as new patches can fix security holes that hackers exploit.
- Automate your update processes if possible, ensuring that you don’t miss critical security enhancements.
- Verify that your antivirus software receives updates automatically to combat the latest malware risks.
- Review update settings on work – related programs to maintain their defenses against digital attacks.
- Ensure that every computer or laptop connected to your network runs the most recent version of its operating system.
- Restart devices when prompted after updates; this step often completes the installation of security features.
- Consult tech support if you’re unsure about an update’s authenticity before proceeding with the installation.
- Schedule maintenance windows during off – hours to avoid disrupting your work with system reboots or installations.
Use strong passwords and two-factor authentication
To further bolster your home office security, it’s imperative to utilize strong passwords and implement two-factor authentication for an added layer of protection. Here are the key steps to ensure the security of your digital assets:
- Craft complex passwords that include a combination of uppercase letters, lowercase letters, numbers, and special characters.
- Refrain from using easily guessable information such as birthdates or pet names in your passwords.
- Employ a reputable password manager to securely store and manage all your passwords.
- Enable two – factor authentication wherever possible to add an extra barrier against unauthorized access.
Security Measures for Employers Dealing with Remote Workforce
Implement VPNs, use multi-factor authentication, and provide comprehensive training for employees on best practices to ensure the security of remote work. Want to learn more about keeping your home office secure? Keep reading for additional tips and insights!
Implement VPNs
To secure data and communications for remote employees, implement VPNs. VPNs encrypt internet traffic, safeguarding information from potential cyber threats. With a VPN in place, sensitive data transmitted between the remote worker’s device and the company’s network remains protected against unauthorized access.
Not only does this offer peace of mind for both employers and employees, but it also ensures that business operations can continue securely.
Moving forward to “Use Multi-Factor Authentication,” another crucial security measure is to fortify digital defenses by implementing multi-factor authentication.
Use multi-factor authentication
Employ multi-factor authentication to add an extra layer of security for accessing sensitive systems and data. This process requires users to provide two or more forms of identification before gaining access, boosting the overall protection of your home office network from unauthorized entry attempts.
By incorporating this additional step along with strong passwords, you can significantly reduce the risk of unauthorized access to your work-related accounts and applications.
Implementing multi-factor authentication will help safeguard your remote work setup against potential cyber threats such as phishing attacks and password breaches. This simple yet powerful security measure aligns with best practices for ensuring data security in a work-from-home environment, providing peace of mind while working in live chat support roles or handling confidential company information remotely.
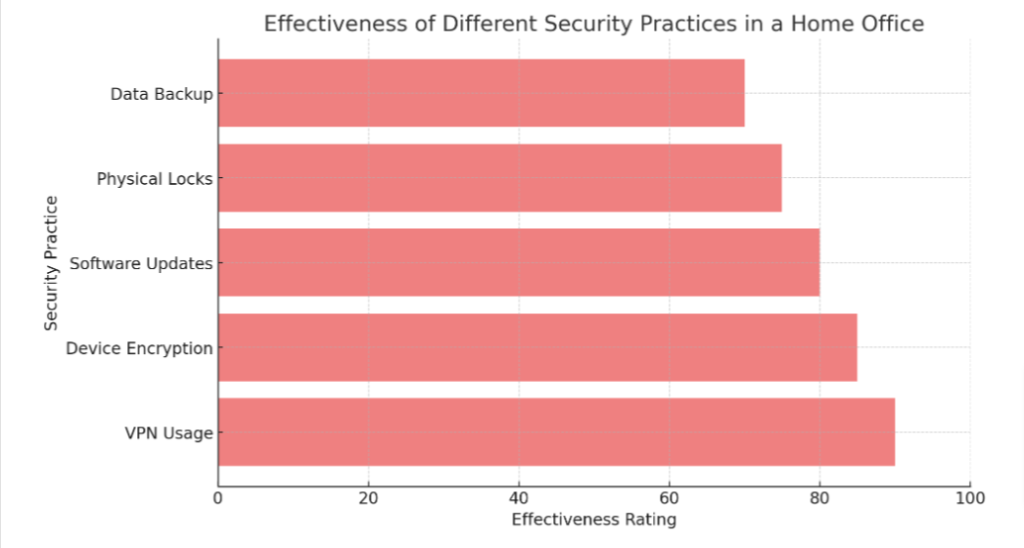
Train employees on best practices
Implement multi-factor authentication to bolster security for remote work. Train employees on best practices to mitigate cybersecurity risks. Provide regular cybersecurity awareness training sessions covering the following:
- Recognizing phishing emails and avoiding clicking on suspicious links or attachments.
- Creating strong, unique passwords for each account, using a combination of letters, numbers, and symbols.
- Securing home Wi – Fi networks with strong passwords and enabling encryption.
- Encrypting sensitive data when storing or transmitting it online.
- Being cautious about sharing confidential information during live chat interactions and ensuring compliance with privacy measures.
Monitor third-party vendors and service providers
To ensure comprehensive security, organizations must monitor third-party vendors and service providers. Here’s how:
- Regularly review contracts and agreements to ensure security protocols are being followed.
- Conduct regular audits of third – party vendors to assess their cybersecurity measures and data protection practices.
- Provide training to vendors on best security practices and expectations for handling sensitive data.
- Use secure channels for sharing information and ensure all communications are encrypted.
- Require third – party vendors to provide regular reports on their security posture and any incidents or breaches.
Top Security Risks for Remote Work
Insecure passwords, phishing emails, unsecured personal devices and networks, and weak backup and recovery systems are some of the top security risks for remote work. It’s important to be aware of these risks and take necessary precautions to protect your data while working remotely.
Insecure passwords
Weak or easily guessable passwords are a common security threat for remote workers. To keep sensitive data safe, it’s crucial to use strong, unique passwords for each account and device.
Implementing two-factor authentication adds an extra layer of security by requiring both a password and a secondary form of verification, such as a code sent to your phone. Keeping passwords confidential and regularly updating them minimizes the risk of unauthorized access to company systems and ensures better protection against potential cyber threats.
Regularly using different keywords is crucial in maintaining online safety while working remotely.
Employers should emphasize the importance of creating secure passwords with their remote workforce as part of cybersecurity best practices. Using password managers can assist employees in generating complex, hard-to-crack passwords without the hassle of memorizing them all, further enhancing their personal cybersecurity measures.
Phishing emails
Be cautious of phishing emails. Educate employees about spotting suspicious email addresses and links to prevent security breaches. Regularly remind your team about the importance of verifying the sender’s address before clicking on any links or downloading attachments to safeguard your organization from potential cyber threats.
Train employees to recognize phishing attempts by emphasizing common red flags such as urgent requests for personal information, generic greetings, and misspelled domain names. Utilize simulated phishing drills to test their understanding and response to such attacks, enhancing their ability to identify and report suspicious emails effectively.
By actively promoting a vigilant approach towards email security, you can fortify your remote workforce against phishing attempts that pose significant risks to data protection.
Unsecured personal devices and networks
To complement protection against phishing emails, securing personal devices and networks is essential for remote work security. Employees should ensure that their personal devices, such as laptops and smartphones, are equipped with updated antivirus software to prevent malware infiltration.
Additionally, it’s crucial to apply encryption methods to secure data on these devices. Moreover, employees must refrain from using public Wi-Fi networks and instead opt for encrypted virtual private network (VPN) connections to safeguard sensitive work-related information.
Regularly updating device operating systems further bolsters the defense against potential security breaches.
By instituting strict measures regarding unsecured personal devices and networks within a remote work setting, employers can significantly mitigate the risk of cyber threats. Encouraging employees to maintain separate accounts for work-related activities on their personal gadgets can help enhance overall cybersecurity readiness.
Weak backup and recovery systems
Weak backup and recovery systems pose a significant threat to the security of remote work. Inadequate data backup can result in critical loss during unforeseen events or cyber-attacks.
Without robust recovery processes in place, employees may struggle to regain access to essential files and resources necessary for seamless work from home operations.
Implementing strong backup protocols, such as regular automated backups and off-site storage, is crucial for protecting sensitive business information. Furthermore, integrating reliable data recovery mechanisms can minimize downtime and ensure continuity in the event of system failures or security breaches.
Conclusion and Additional Tips
Invest in cybersecurity awareness training and use password managers and encryption to protect your data. Regularly run software updates, secure video meetings, and be cautious with wireless networks.
Keep work and personal devices separate for added security.
Invest in cybersecurity awareness training
One essential step for both employees and employers to bolster remote work security is through investing in cybersecurity awareness training. This type of training equips employees with the knowledge and skills to identify potential threats such as phishing emails and insecure networks, helping them understand best practices for data protection while working remotely.
Additionally, it instills a culture of vigilance within the organization, ensuring that all team members are actively engaged in safeguarding sensitive information from cyber threats.
By investing in cybersecurity awareness training, organizations can significantly reduce the risk of data breaches and security incidents associated with remote work. This proactive approach empowers employees to take responsibility for their role in maintaining a secure work-from-home setup, ultimately contributing to enhanced overall network security and privacy measures.
Use password managers and encryption
In addition to investing in cybersecurity awareness training, it’s crucial for employees and employers to utilize password managers and encryption. Password managers offer a secure way to generate and store complex passwords for all accounts, reducing the risk of unauthorized access.
By employing encryption techniques, sensitive data transmitted or stored within home offices can be safeguarded from potential cyber threats. These tools are essential components of an effective security strategy when working remotely, helping to mitigate the risks associated with online work environments.
Regularly run software updates
To enhance the security of your home office, it is important to regularly run software updates. This helps in safeguarding your devices and networks against potential vulnerabilities. Here are key measures to ensure effective software updates and protection:
- Set up automatic updates for operating systems, antivirus software, and applications to ensure that the latest patches and security features are installed promptly.
- Monitor and review update notifications from software vendors regularly, ensuring that critical security fixes are not delayed.
- Encourage employees to restart their devices after updates to ensure that all changes take effect.
- Utilize endpoint management solutions to centrally manage software updates across remote work devices, facilitating streamlined control and accountability.
- Conduct regular assessments of the update process to identify any gaps or issues that need attention, maintaining a proactive approach to security maintenance.
Secure video meetings and be cautious with wireless networks
To secure video meetings and be cautious with wireless networks:
- Use a secure, password-protected video conferencing platform that offers end-to-end encryption to prevent unauthorized access to your conversations.
- Always verify the attendees before joining a video meeting to avoid potential security breaches.
- Avoid using public Wi-Fi networks for video calls; instead, connect to a secure, password-protected network or use a virtual private network (VPN) for added protection.
- Regularly update the software and firmware of your camera and microphone to protect against potential vulnerabilities.
- Disable features like screen sharing and file transfer in video conferencing tools to prevent unauthorized data access during meetings.
Keep work and personal devices separate.
To secure your home office, keep work and personal devices separate. This helps prevent potential data breaches or security risks associated with using the same devices for both work and personal activities.
By maintaining this separation, you can minimize the chances of unauthorized access to sensitive work-related information while also protecting your personal data from any potential workplace security vulnerabilities.
Keeping work and personal devices separate is crucial for maintaining a secure home office setup. It ensures that confidential company data remains protected, reduces the risk of malware infections spreading between work and personal accounts, and safeguards against any compromise of sensitive information in either context.

